By: Tonya Mead, PhD, MBA, M.Ed, CFE, CHFI, PI
This is the time for which kids have been waiting! It is also the time for parents to increase vigilance on the toys and games used by their children over the summer holiday. Recognizing this, school-based Chief Information Security Officers (CISO), penetration testers and ethical hacking experts conduct vulnerability analysis and threat assessments, for prevention and mitigation. Kids aren’t the only prey. Adult games and apps can be embedded with code making personal data vulnerable to cyber crime. Here is a compilation of case studies on cyber threats.
It is a distillation of a presentation that was prepared for the Federal Information Systems Security Educators Association and the National Institutes of Standards and Technology. It provides an overview of the cyber threats corresponding with children’s toys and adult games linked to the internet and the dangers of hacking for nefarious purposes.
My Melody and Hello Kitty
Image 1.
My Melody (a red-hooded rabbit), borrows a similar story line as the American version of ‘Little Red Robin Hood’ and the best friend of Hello Kitty, are CGI animated characters that are popular in Asia. Their images are licensed on merchandise targeting pre-adolescent girls of the Y Generation.
According to Melanie Matchette of Western Michigan University, “The Hello Kitty brand is available in over seventy countries with more than 50,000 products available in 15,000 Sanrio retail stores.” (Matchette, p. 5). In fact, Matchette explains that the popularity of the Hello Kitty merchandise stems from the celebrity endorsements of Christina Aguilera, Lisa Loeb, Tyra Banks, and Mariah Carey in the 1990s. By 2014, Hello Kitty jewelry was endorsed as a premium brand by Kimora Lee Simmons, former spouse of the rap icon Russell Simmons.
Known Cyber Threat
Why is this information important for cyber sleuths? A leaked customer database exposing more than 3.3 million user accounts for Sanriotown.com and other Sanrio-owned websites like hellokitty.com and mymelody.com became public in 2017. Almost two hundred thousand tween and teen fans were counted among the victims. The breached data involved the full names (first, middle and last), decipherable dates of birth, email addresses, and encrypted passwords, along with password reset questions and answers.
Play Station and X Box
NewZoo in its Global Games Market Report readjusted its forecast “ $116 billion in game software revenues,” at the end of 2017 which represented “ $7.1 billion higher than [their] previous estimate.” Which firms dominate the market? As of July 2016, Sony and Microsoft control to gaming console market. According to Kettunen and separately Vigneswar Sankara of Deakin Business School, Sony’s Play station “rules the market with having over 54% of all console sales, Microsoft is second with 28% and Nintendo third with 17%.” (Kettunen, p. 9).
How massive is the gaming industry? Again, NewZoo states with confidence that the gaming industry “ generate more than three times the $38.6 billion in movie ticket sales” and is within striking distance of the global sports business, which is “estimated to total between $130 and $150 billion depending on the definition and reporting source.” (para 7).
This includes media rights sales, sponsorships, merchandise, and ticketing. Two years later, hackers stole the confidential information of almost three million users from two unofficial but popular gaming forums, Play Station and X Box.
Image 2. 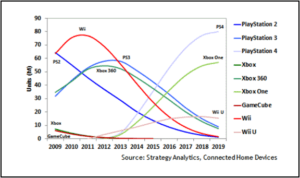
Video games are not just for kids. Who is the average gamer? The Entertainment Software Association reports that the average gamer is 35 years old. “Sixty-five percent of U.S. households are home to at least one person who plays 3 or more hours of video games a week.”) And, “there are an average of 1.7 gamers in each game-playing U.S. household.” (p.7). Finally, “53 percent of the most frequent gamers play multi-players games at least once per week, spending an average of 6 hours playing with others online and 5 hours playing with others in person.” (p.8).
Known Cyber Threat
Image 3. 
Recognizing the popularity of forums frequented by gamers seeking multi-player partners, hackers gained access to online gaming forums called Xbox 360 ISO and PSP ISO. These forums enable gamers to share files and download free and pirated copies of games. Cyber hackers stole the confidential information of 2.5 million users. Hackers obtained email addresses, passwords and IP addresses (a unique string of numbers separated by periods that identifies the specific computer used by gamers via the Internet Protocol for communicating over a network). of the gamers.
Hello Barbie
InfoScout describes Barbie consumers as “generally very high income, Hispanic, and lower middle age. Barbie consumers are more likely to purchase Barbie during larger pantry stocking trips.” (Para 1, line 1).
Image 4. 

What is interesting about this toy and the expansionary vision of its manufacturer, Mattel? The company is aggressively pursuing its goal “to win over moms, and while they’re at it, dads too,” says AdAge. To reach this untapped market, Mattel created Hello Barbie which represented the first interactive Barbie doll. On its two minute video posted to YouTube, advertisers proudly exclaimed, “finally a Barbie doll that you can talk to, and she will talk back! She also adapts to you and learns your likes and dislikes.”
Known Cyber Threat
Are cyber security experts in the field the only people sensing the danger? According to privacy advocates, “the doll is always listening meaning that it sends audio files to a cloud server for processing and storage.” Further, the Wi-Fi (technology for wireless local area networking) and internet connected doll has been proven by Matt Jakubowski, a security researcher to be vulnerable to hacking. While it responds to a child’s voice (or any voice that matter), it stores the recorded information about the child, family, friends and acquaintances (like a favorite class or grandmother’s name) for future conversations. Hackers can then access the stored data, audio files and take control of Barbie’s internalized microphone to listen in on children’s conversations.
Teddy Ruxpin and Adorable Teddy Bear
Teddy Ruxpin, a popular toy in the 1980s, revolutionized the traditional cuddly teddy bear. At the time it could ”talk, blink, and tell stories.” Its primary selling feature was the implantation of a hidden cassette tape deck that played songs. By 2017, Wicked Cool Toys re-designed and re-introduced Teddy Ruxpin as part-toy, part-computer built with 4 GB hard drive and eyes composed of “LCD screens that blink, flash, and show pictures.” He’s also linked to a free computer application that once unlocked allows kids to access 10 additional stories for following along with a tablet or Smartphone.
Image 5. 
Adorable teddy bear, on the other hand is an unrelated product that connects to a remote ‘secure’ server on the internet. It has the ability to store a child’s name for future interactions.
Known Cyber Threat
Hackers took advantage of internet connected microphone and recorded messages by gaining access to 2 million parent and child recordings (messages) and 800,000 user account credentials maintained by the toy company, Spiral Toys. The criminals then informed the Spiral Toy that it would lock down the data thereby making it inaccessible until they (the criminal hackers) had received a ransom payment from Spiral Toys. Incidentally, journalists have allegedly reported that the company was contacted prior to the hacking incident and told on multiple occasions that customer data was visible, online and accessible for “anyone to grab — yet the data remained up for at least a week with evidence suggesting that it was stolen more than once.” (Para 2).
One reason why the information was particularly valuable in the black market is that hackers could use stored information (like a child’s name and birthday) to determine a family’s password, as names and birthdates are common pass codes for many people.
V Tech
V Tech, a Hong Kong based toy-maker produces hundreds of popular toys aimed at the toddler, pre-school market and specializes in interactive toys. Some of these toys include: KidiBuzz electronic handheld game, KidiZoom Smartwatch, Touch and Learn Activity Desk, and KidiZoom 180 Action Camera, among others.
Image 6.
Known Cyber Threat
What is interesting about V Tech? Motherboard revealed that almost two hundred GB data consisting of confidential information, photos, chat logs from the Kid Connect Service, and audio recordings were accessed from the VTech system Learning Lodge computer applications. In late November, a hacker pulled more than 11 million users’ data from the gadget maker Vtech, of which nearly 6.4 million were kids, according to the company.
As a result, in the start of 2018, the Federal Trade Commission (FTC) and V Tech reached a $650,000 settlement in which the “company was charged with illegally collecting kids’ info and then failing to protect it from hackers.”
Exploitation Factors
In summary, the case studies presented above demonstrate that cyber criminals, syndicates and hackers whenever possible will use viruses, coding, backdoors to seek out the following information from toys and games for eventual resale on the Black market.
- Personally identifying information such as full name, nick name, birth dates, physical address, phone numbers, and email contacts
- Photo, video (webcams), audio recordings and call logs
- Stored data about the device’s physical location and internet protocol address
- Internet usage data (time, date stamps, peak usage periods)
- Calendar data
- Passwords, user names, access codes
Recommendations for Cyber Security Professionals
As a concerned parent, former educator and cyber security professional, I regularly inform others on ways in which we can join together to help companies and governmental agencies reduce the threat of unintentional cyber security hacking and data breaches experienced by employees and their families. See below a few recommendations.
- Inform employees of the Children’s Online Privacy Protection Act. This law requires toy makers and gamers targeting kids to notify parents and obtain consent when collecting children’s information online. It also requires companies to take reasonable steps to protect the information and data collected.
- Train employees on maintaining vigilance at work and at home: refrain from downloading free web and computer applications, change passwords often, use different passwords for different applications, disable Wi-Fi connections from children’s toys, shield webcam and photographic capabilities from automated use, read and review data policies for any and all applications downloaded, utilize private screens and ad blocking software to disable the tracking of internet traffic.
- Establish a regular training schedule and establish an annual in-house certification program to impart knowledge to employees about internet safety and work and at home.
About Tonya Mead
Tonya J. Mead, PhD, MBA, M.Ed, CHFI, CFE, PI, is the founder of Shared Knowledge LLC a private security and detective agency. Dr. Mead, formerly a certified K-12 Administrator and School Psychologist, is author of Fraud in Education: Beyond the Wrong Answer and president of Shared Knowledge, LLC http://ishareknowledge.com If you like her work, please support her at Patreon.
Other articles you might like
- Smartphone use, sleep and your child
- Medicaid kids and drugs
- How to grow your child’s brain
- Brain elasticity and children
- Prevent teen suicide
- School violence and suicide
- 10 Tips for parents to prevent suicide
- Create calmness in chaos
